IMPLEMENTATION OF SHA-1 ALGORITHM using JAVA

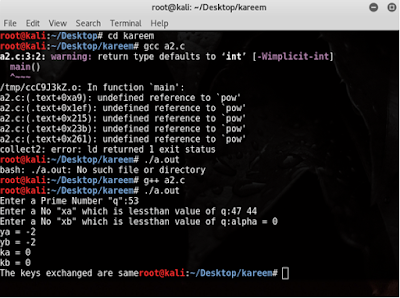
AIM: To write a java program to calculate the message digest of a text using the SHA-1 algorithm ALGORITHM: Step 1: Input the plain text Step 2: Append padding bits Step 3: Append length Step 4:Initialize buffer. Step 5: Process message in 512-bit (16word)blocks Step 6: Encrypted in hexa decimal format Step 7: Display the encrypted text. PROGRAM: importjava.security.*; public class SHA1 { public static void main(String[] a) { try { MessageDigest md = MessageDigest.getInstance("SHA1"); System.out.println("Message digest object info: "); System.out.println(" Algorithm = " +md.getAlgorithm()); System.out.println(" Provider = " +md.getProvider()); System.out.println(" ToString = " +md.toString()); String input = ""; md.update(input.getBytes()); byte[] output = md.digest(); System.out.println(); System.out.println("SHA1(\""+...